
CCNA 200-301 – Configure and Verify Data and Voice VLANs
June 24, 2020
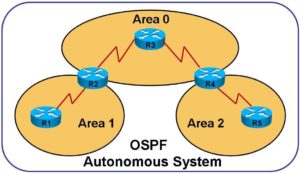
CCNA 200-301 – Best Way to OSPFv2 Troubleshooting
June 22, 2020
CCNA 200-301 – OSPF Configuration Basics
April 18, 2020
Palo Alto Networks Firewall (PCNSE) Configuration
April 16, 2020
How To Change the Palo Alto Networks Firewall Password
April 15, 2020
Factory Reset Palo Alto Networks Firewall The Easy Way
April 13, 2020
